Compellent has been shipping its SAN appliances to small to medium-sized companies for three years, growing from $4 million in annual sales to more than $23 million last year. Part of the reason for that growth, says cofounder John Guider, is that Compellent executives have recognized the value of making an open source operating system one of the building blocks of the company’s SAN offerings.
Monthly Archives: November 2007
Legend has it that a Moleskine notebook and a pen were the tools of choice for Chatwin and Hemingway — but that’s because they didn’t have Writer’s Café. Designed specifically for writing professionals, this application suite includes a few clever features that make it a must-have tool, whether you write for a living or for fun. Although the Writer’s Café developers state that it’s most suited for writing fiction, novels, and short stories, you can easily use it for all kinds of writing activities.
In theory, GDB, the GNU debugger, can ease the chore of debugging applications running on a Linux-based embedded system. In practice, setting up GDB for this task is a bit of a challenge; it takes some work, and there are some technical hurdles to overcome. However, the benefits of having a way to methodically debug a program instead of guessing what’s wrong with it far outweigh the effort involved. Here are some tips for easing the difficulties.
Using KVM On Ubuntu 7.10 (Gutsy Gibbon)
In this HowTo I’ll explain how to install and use KVM for running
your services in virtual machines. KVM (Kernel-based Virtual Machine)
is a Linux kernel virtualization technique that provides full
virtualization by using Intel VT (Vanderpool) or AMD-V (Pacifica).
How To Install VMware Server 1.0.4 On Ubuntu 7.10 (Gutsy Gibbon)
This tutorial provides step-by-step instructions about how to
install the free VMware Server on an Ubuntu 7.10 (Gutsy Gibbon) system.
With VMware Server you can create and run guest operating systems
(“virtual machines”) such as Linux, Windows, FreeBSD, etc. under a host
operating system. This has the benefit that you can run multiple
operating systems on the same hardware which saves a lot of money, and
you can move virtual machines from one VMware Server to the next one
(or to a system that has the VMware Player which is also free).
Introduction
Do you think you’re safe if you type https :// before paypal.com? I hope you’ll think twice before you login from a computer connected to a wireless network after reading this guide. Let’s start at the beginning. Let’s say you have an evil neighbour who wants your paypal credentials. He buys himself a nice laptop with a wireless card and, if you are using a wep encryption, he cracks your wep code (click here to see how). After cracking the key he logs into your network. Maybe you always allowed him to use your network because you thought it can’t do any harm to your computer. You aren’t sharing any folders so what’s the problem? Well, in the next few steps I’m going to describe the problem.
The guide
1. Let’s assume your neighbour uses linux to crack your wep key. After cracking it, he installs ettercap (http://ettercap.sourceforge.net/) on his linux system. If you want to do this at home, I would recommend you to download BackTrack because it already has everything installed. Look at the WEP cracking guide I mentioned above for more info about BackTrack. If you want to install it on your own linux distribution, download the source and install it with the following commands:
$ tar -xzvf ettercap-version.tar.gz
$ make
$ make install
2. After installing, you need to uncomment some code to enable SSL dissection. Open up a terminal window and type “nano /usr/local/etc/etter.confâ€, without the quotes. Scroll down using your arrow keys until you find this piece of code:
# if you use iptables:
# redir_command_on = “iptables -t nat -A PREROUTING -i %iface -p tcp –dport %port -j REDIRECT –to-port %rportâ€
# redir_command_off = “iptables -t nat -D PREROUTING -i %iface -p tcp –dport %port -j REDIRECT –to-port %rportâ€
You need to uncomment the last two lines.
# if you use iptables:
redir_command_on = “iptables -t nat -A PREROUTING -i %iface -p tcp –dport %port -j REDIRECT –to-port %rportâ€
redir_command_off = “iptables -t nat -D PREROUTING -i %iface -p tcp –dport %port -j REDIRECT –to-port %rportâ€
3. Press CTRL+O, press enter to safe the file and then press CTRL+X.
4. Boot Ettercap and click on Sniff > Unified Sniffing > type in your wireless interface and press ok.
5. Press CTRL+S to scan for hosts
6. Go to MITM > ARP poisoning, select sniff remote connections and press ok.
7. Now you (and your neighbour!) can start sniffing! Press start > start sniffing. Walk to another computer on your network and open up paypal or any other site where you need to type in an username/password (gmail, hotmail, digg.com, etc.). All credentials will appear on the computer running Ettercap!
8. When you’re done, don’t just close Ettercap, but go to Start > Stop Sniffing, and then go to MITM > Stop mitm attack(s).
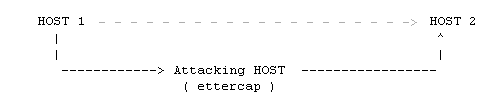
But how does all this stuff work?
Look at the following scheme:
Normally when you type in a password, host 1 (your computer) directly connects to host 2 (your modem or router). But if someone launced Ettercap on your network, host 1 isn’t sending it’s passwords to host 2, but to the Attacking host, the host that’s running Ettercap! The attacking host sends everything to Host 2. This means that host 1 isn’t noticing anything! Exactly the same happens with everything that host 2 is sending. Host 2 doesn’t send packets directly to host 1, but forst to the attacking host.
Almost all websites have them, and they are just extraordinary ugly: Dotted borders around text links. They show up when you click a link and won’t go away till you clicked somewhere else, reloaded the page or moved to another page:

Yes, I know that you saw that before. But why are all those sites displaying those ugly borders? I don’t know, because you don’t need to know any advanced techniques to remove the border! Just add the following code to your CSS document:
a {
outline: none;
}
And gone are the dotted borders!
But does that validate?
It’s easy to think that everyone isn’t using this because it doesn’t validate, though it does validate! Check it out on the W3C Validator on your page if you don’t believe me.
But why isn’t everyone using this?
Because most people don’t know that it is possible In the past it was necessary to have the dotted border around licked links to see if you actually clicked it or not (in he past we had sow computers, so it took a while before the thing actually started downloading the new site). Today we don’t need that anymore in most cases, so please add this code to your Cascading Style Sheets and stop the ugliness!
The times of slow internet connections are over and most webmasters don’t have to worry about long loading times anymore. This means that background music becomes more popular. Sometimes you hear a song you like on a site, but you don’t know how the song is called and/or can’t find it anywhere on the world wide web. If the song is embedded with a Flash file, or if the whole site is Flash, most people think that it’s impossible to download the song because they can’t find a link to it. In this post I’ll prove the opposite. I’ll use the website 3121.com/jam/. It’s Prince’s official website, which features a new Jam of the Week every week. Since I’m a big fan I want the songs on my iPhone, but there isn’t a download link on the site! The following steps allow me to download the song, without a download link.
1. Download the web browser Safari (OSX or Windows) and start it.
2. Browse to the site with the embedded song (in this example: 3121.com/jam/)
3. In Safari’s toolbar, click Window > Activity
4. Scroll to the mp3 file, if there’s more than one, use common sense in combination with the file size and file name to find the right one. Double click it.
5. If the download starts automatically, the song will appear in your downloads folder, if it opens Quicktime, hit the little arrow and select safe as source. If it does something else, copy paste the URL in Firefox and go to file > save as.
That’s it! This little trick works for all embedded things (youtube video’s, background music, vodcasts, podcasts etc.)
If you know a better way, please leave a comment, though I think that this beats all youtube download pages/plugins (since it won’t go down after 2 days nor need to be constantly updated)
I have used X10 modules on assorted lights and devices for home automation for several years, and although the remote control facet has always worked well, tying the system into my Linux boxes has never been easy. Numerous small, typically one-person X10 controller projects have come and gone. But one application has survived: Heyu. It runs on desktop Linux machines without requiring the overhead of a Web or database server, and it enables direct X10 control, event scheduling, and more.
Linux is an excellent platform for network administration. If you want to monitor your network traffic, you can find many tools — some accessible from a Web interface, others using a graphical interface — but nothing beats the speed of the command line. Command-line tools are also useful in shell scripts, where they can help you perform complex tasks. Here’s a handful of my favorites for monitoring network traffic.