This tutorial shows how to set up a Ubuntu Gutsy Gibbon (Ubuntu 7.10) based server that offers all services needed by ISPs and hosters: Apache web server (SSL-capable), Postfix mail server with SMTP-AUTH and TLS, BIND DNS server, Proftpd FTP server, MySQL server, Courier POP3/IMAP, Quota, Firewall, etc. This tutorial is written for the 32-bit version of Ubuntu Gutsy Gibbon, but should apply to the 64-bit version with very little modifications as well.
I will use the following software:
- Web Server: Apache 2.2
- Database Server: MySQL 5.0
- Mail Server: Postfix
- DNS Server: BIND9
- FTP Server: proftpd
- POP3/IMAP: I will use Maildir format and therefore install Courier-POP3/Courier-IMAP.
- Webalizer for web site statistics
In the end you should have a system that works reliably, and if you like you can install the free webhosting control panel ISPConfig (i.e., ISPConfig runs on it out of the box).
I want to say first that this is not the only way of setting up such a system. There are many ways of achieving this goal but this is the way I take. I do not issue any guarantee that this will work for you!
1 Requirements
To install such a system you will need the following:
- the Ubuntu Gutsy Gibbon server CD, available here: http://releases.ubuntu.com/7.10/ubuntu-7.10-server-i386.iso
- a fast internet connection.
2 Preliminary Note
In this tutorial I use the hostname server1.example.com with the IP address 192.168.0.100 and the gateway 192.168.0.1. These settings might differ for you, so you have to replace them where appropriate.
3 The Base System
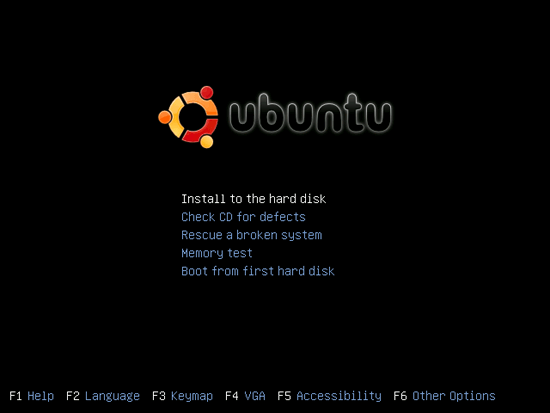
Insert your Ubuntu install CD into your system and boot from it. Select Install to the hard disk:
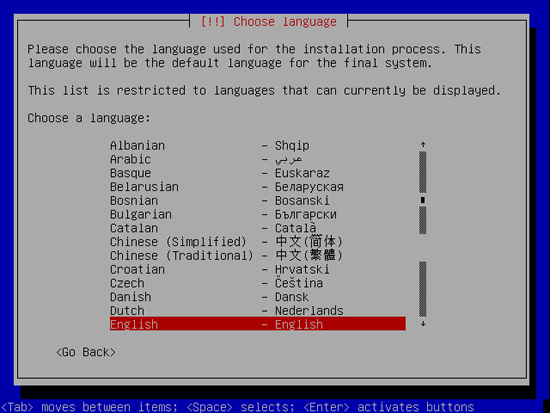
The installation starts, and first you have to choose your language:
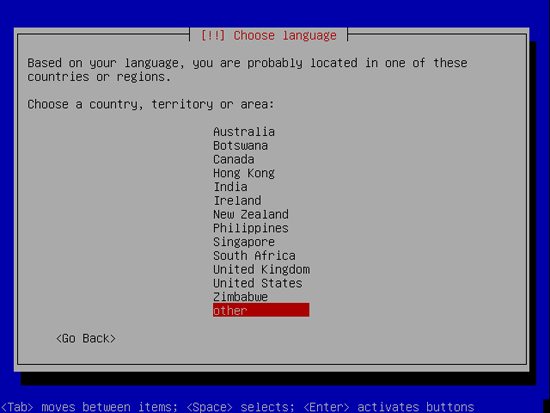
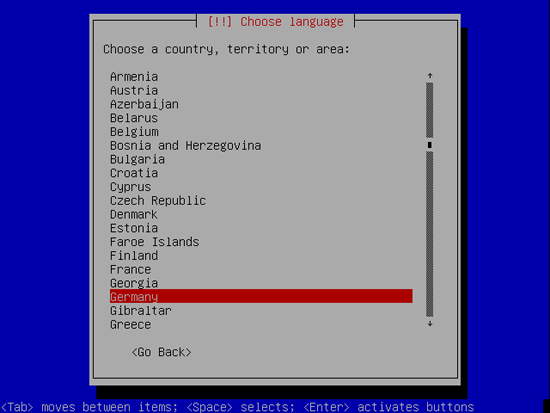
Then select your location:
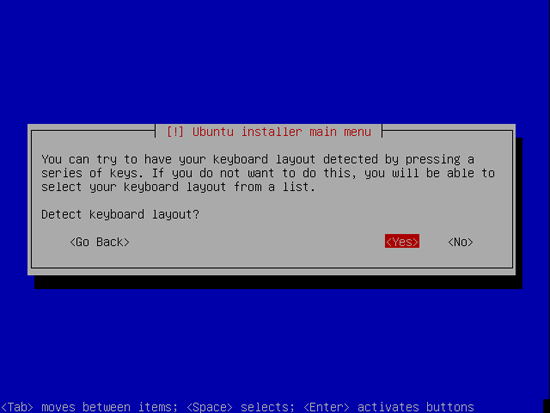
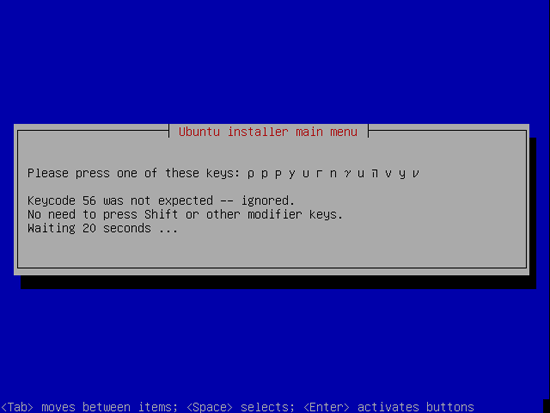
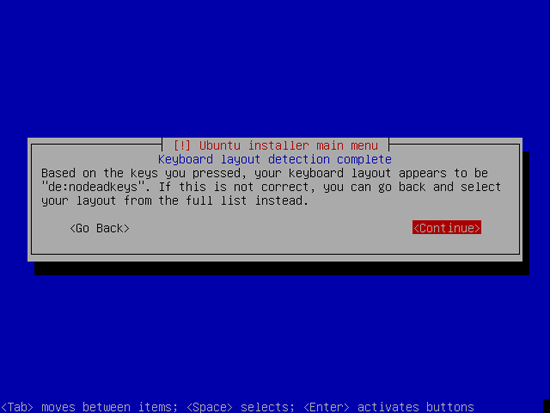
Choose a keyboard layout (you will be asked to press a few keys, and the installer will try to detect your keyboard layout based on the keys you pressed):
The installer checks the installation CD, your hardware, and configures the network with DHCP if there is a DHCP server in the network:
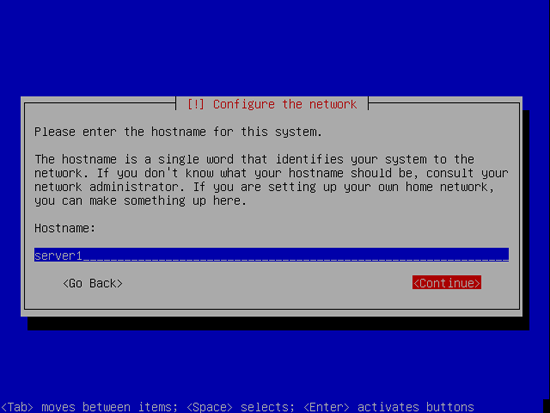
Enter the hostname. In this example, my system is called server1.example.com, so I enter server1:
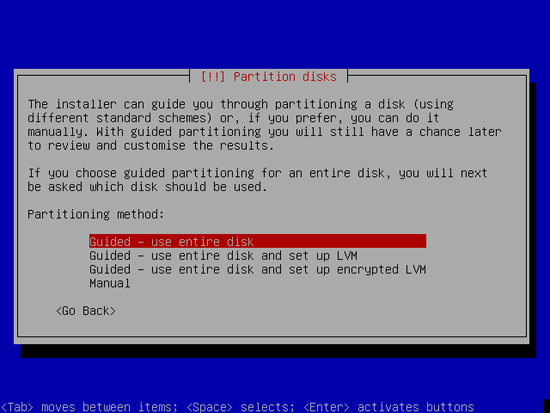
Now you have to partition your hard disk. For simplicity’s sake I will create one big partition (with the mount point /) and a little swap partition so I select Guided – use entire disk (of course, the partitioning is totally up to you – if you like, you can create more than just one big partition, and you can also use LVM):
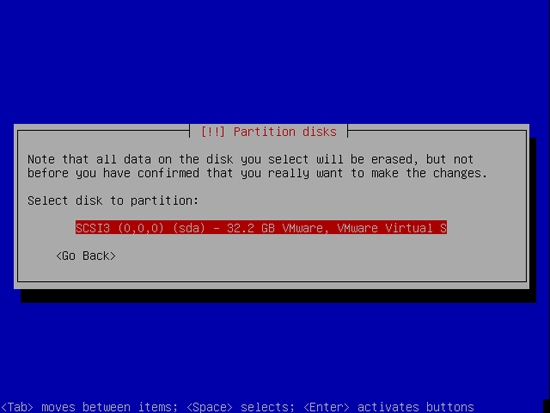
Select the disk that you want to partition:
When you’re finished, hit Yes when you’re asked Write the changes to disks?:
Afterwards, your new partitions are being created and formatted:
Configure your system’s clock. Normally UTC is a good choice:
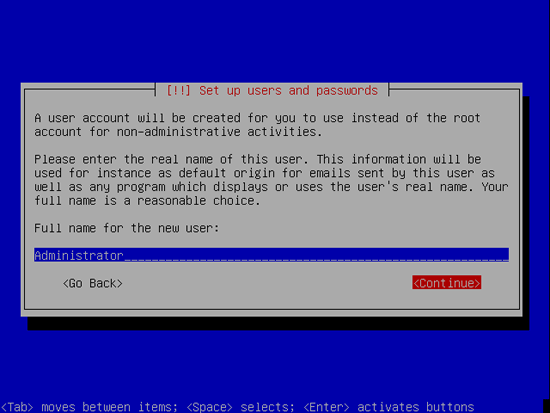
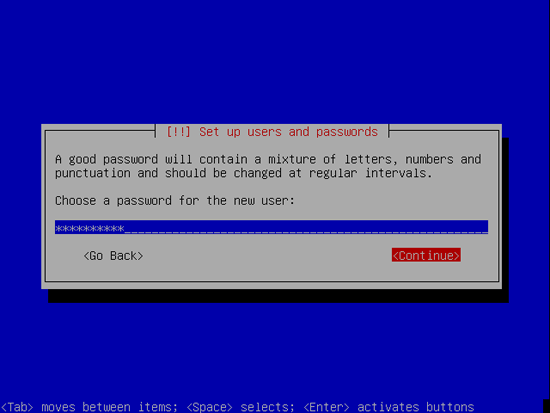
Create a user, for example the user Administrator with the user name administrator (don’t use the user name admin as it is a reserved name on Gutsy Gibbon):
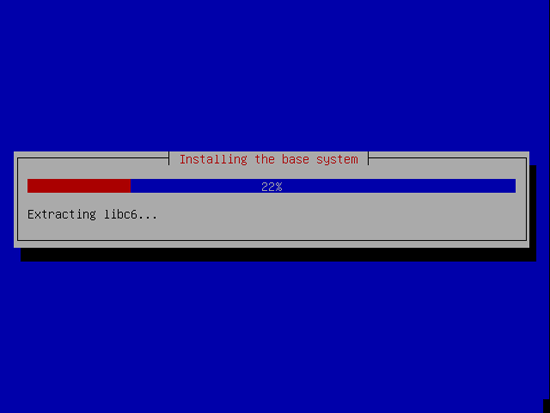
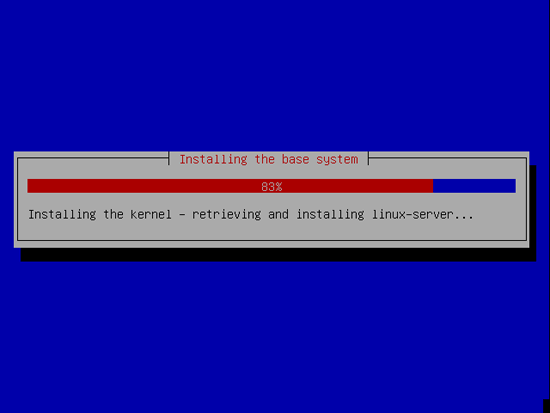
Now the base system is being installed:
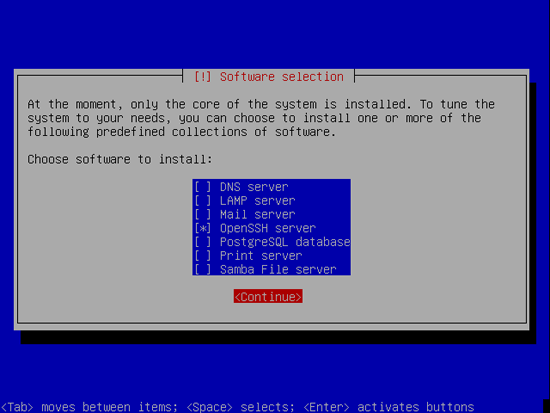
We need a DNS, mail, and LAMP server, but nevertheless I don’t select any of them now because I like to have full control over what gets installed on my system. We will install the needed packages manually later on. The only item I select here is OpenSSH server so that I can immediately connect to the system with an SSH client such as PuTTY after the installation has finished:
The installation continues:
The GRUB boot loader gets installed:
The base system installation is now finished. Remove the installation CD from the CD drive and hit Continue to reboot the system:
On to the next step…
4 Enable The root Account
After the reboot you can login with your previously created username (e.g. administrator). Because we must run all the steps from this tutorial as root user, we must enable the root account now.
Run
sudo passwd root
and give root a password. Afterwards we become root by running
su
5 Install The SSH Server (Optional)
If you did not install the OpenSSH server during the system installation, you can do it now:
apt-get install ssh openssh-server
From now on you can use an SSH client such as PuTTY and connect from your workstation to your Ubuntu Gutsy Gibbon server and follow the remaining steps from this tutorial.
6 Install vim-full (Optional)
I’ll use vi as my text editor in this tutorial. The default vi program has some strange behaviour on Ubuntu and Debian; to fix this, we install vim-full:
apt-get install vim-full
(You don’t have to do this if you use a different text editor such as joe or nano.)
7 Configure The Network
Because the Ubuntu installer has configured our system to get its network settings via DHCP, we have to change that now because a server should have a static IP address. Edit /etc/network/interfaces and adjust it to your needs (in this example setup I will use the IP address 192.168.0.100):
vi /etc/network/interfaces
# This file describes the network interfaces available on your system# and how to activate them. For more information, see interfaces(5).# The loopback network interface auto lo iface lo inet loopback # The primary network interface auto eth0 iface eth0 inet static address 192.168.0.100 netmask 255.255.255.0 network 192.168.0.0 broadcast 192.168.0.255 gateway 192.168.0.1 |
Then restart your network:
/etc/init.d/networking restart
Then edit /etc/hosts. Make it look like this:
vi /etc/hosts
127.0.0.1 localhost.localdomain localhost192.168.0.100 server1.example.com server1# The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters ff02::3 ip6-allhosts |
Now run
echo server1.example.com > /etc/hostname
/etc/init.d/hostname.sh start
Afterwards, run
hostname
hostname -f
Both should show server1.example.com now.
8 Edit /etc/apt/sources.list And Update Your Linux Installation
Edit /etc/apt/sources.list. Comment out or remove the installation CD from the file and make sure that the universe and multiverse repositories are enabled. It should look like this:
vi /etc/apt/sources.list
## deb cdrom:[Ubuntu-Server 7.10 _Gutsy Gibbon_ - Release i386 (20071016)]/ gutsy main restricted#deb cdrom:[Ubuntu-Server 7.10 _Gutsy Gibbon_ - Release i386 (20071016)]/ gutsy main restricted # See http://help.ubuntu.com/community/UpgradeNotes for how to upgrade to # newer versions of the distribution. deb http://de.archive.ubuntu.com/ubuntu/ gutsy main restricted deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy main restricted ## Major bug fix updates produced after the final release of the ## distribution. deb http://de.archive.ubuntu.com/ubuntu/ gutsy-updates main restricted deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy-updates main restricted ## N.B. software from this repository is ENTIRELY UNSUPPORTED by the Ubuntu ## team, and may not be under a free licence. Please satisfy yourself as to ## your rights to use the software. Also, please note that software in ## universe WILL NOT receive any review or updates from the Ubuntu security ## team. deb http://de.archive.ubuntu.com/ubuntu/ gutsy universe deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy universe deb http://de.archive.ubuntu.com/ubuntu/ gutsy-updates universe deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy-updates universe ## N.B. software from this repository is ENTIRELY UNSUPPORTED by the Ubuntu ## team, and may not be under a free licence. Please satisfy yourself as to ## your rights to use the software. Also, please note that software in ## multiverse WILL NOT receive any review or updates from the Ubuntu ## security team. deb http://de.archive.ubuntu.com/ubuntu/ gutsy multiverse deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy multiverse deb http://de.archive.ubuntu.com/ubuntu/ gutsy-updates multiverse deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy-updates multiverse ## Uncomment the following two lines to add software from the 'backports' ## repository. ## N.B. software from this repository may not have been tested as ## extensively as that contained in the main release, although it includes ## newer versions of some applications which may provide useful features. ## Also, please note that software in backports WILL NOT receive any review ## or updates from the Ubuntu security team. # deb http://de.archive.ubuntu.com/ubuntu/ gutsy-backports main restricted universe multiverse # deb-src http://de.archive.ubuntu.com/ubuntu/ gutsy-backports main restricted universe multiverse ## Uncomment the following two lines to add software from Canonical's ## 'partner' repository. This software is not part of Ubuntu, but is ## offered by Canonical and the respective vendors as a service to Ubuntu ## users. # deb http://archive.canonical.com/ubuntu gutsy partner # deb-src http://archive.canonical.com/ubuntu gutsy partner deb http://security.ubuntu.com/ubuntu gutsy-security main restricted deb-src http://security.ubuntu.com/ubuntu gutsy-security main restricted deb http://security.ubuntu.com/ubuntu gutsy-security universe deb-src http://security.ubuntu.com/ubuntu gutsy-security universe deb http://security.ubuntu.com/ubuntu gutsy-security multiverse deb-src http://security.ubuntu.com/ubuntu gutsy-security multiverse |
Then run
apt-get update
to update the apt package database and
apt-get upgrade
to install the latest updates (if there are any).
9 Change The Default Shell
/bin/sh is a symlink to /bin/dash, however we need /bin/bash, not /bin/dash. Therefore we do this:
ln -sf /bin/bash /bin/sh
If you don’t do this, the ISPConfig installation will fail.
10 Install Some Software
Now we install a few packages that are needed later on. Run
apt-get install binutils cpp fetchmail flex gcc libarchive-zip-perl libc6-dev libcompress-zlib-perl libdb4.3-dev libpcre3 libpopt-dev lynx m4 make ncftp nmap openssl perl perl-modules unzip zip zlib1g-dev autoconf automake1.9 libtool bison autotools-dev g++ build-essential
(This command must go into one line!)
11 Quota
(If you have chosen a different partitioning scheme than I did, you must adjust this chapter so that quota applies to the partitions where you need it.)
To install quota, run
apt-get install quota
Edit /etc/fstab. Mine looks like this (I added ,usrquota,grpquota to the partition with the mount point /):
vi /etc/fstab
# /etc/fstab: static file system information. # # <file system> <mount point> <type> <options> <dump> <pass> proc /proc proc defaults 0 0 # /dev/sda1 UUID=9fc157ff-975c-4f20-9fef-6a70085abdbd / ext3 defaults,errors=remount-ro,usrquota,grpquota 0 1 # /dev/sda5 UUID=48fb7dd8-f099-4d63-ac1b-30e886ac7436 none swap sw 0 0 /dev/scd0 /media/cdrom0 udf,iso9660 user,noauto,exec 0 0 /dev/fd0 /media/floppy0 auto rw,user,noauto,exec 0 0 |
To enable quota, run these commands:
touch /quota.user /quota.group
chmod 600 /quota.*
mount -o remount /
quotacheck -avugm
quotaon -avug
12 DNS Server
Run
apt-get install bind9
For security reasons we want to run BIND chrooted so we have to do the following steps:
/etc/init.d/bind9 stop
Edit the file /etc/default/bind9 so that the daemon will run as the unprivileged user bind, chrooted to /var/lib/named. Modify the line: OPTIONS=”-u bind” so that it reads OPTIONS=”-u bind -t /var/lib/named”:
vi /etc/default/bind9
OPTIONS="-u bind -t /var/lib/named" # Set RESOLVCONF=no to not run resolvconf RESOLVCONF=yes |
Create the necessary directories under /var/lib:
mkdir -p /var/lib/named/etc
mkdir /var/lib/named/dev
mkdir -p /var/lib/named/var/cache/bind
mkdir -p /var/lib/named/var/run/bind/run
Then move the config directory from /etc to /var/lib/named/etc:
mv /etc/bind /var/lib/named/etc
Create a symlink to the new config directory from the old location (to avoid problems when bind gets updated in the future):
ln -s /var/lib/named/etc/bind /etc/bind
Make null and random devices, and fix permissions of the directories:
mknod /var/lib/named/dev/null c 1 3
mknod /var/lib/named/dev/random c 1 8
chmod 666 /var/lib/named/dev/null /var/lib/named/dev/random
chown -R bind:bind /var/lib/named/var/*
chown -R bind:bind /var/lib/named/etc/bind
We need to modify /etc/default/syslogd so that we can still get important messages logged to the system logs. Modify the line: SYSLOGD=”” so that it reads: SYSLOGD=”-a /var/lib/named/dev/log”:
vi /etc/default/syslogd
# # Top configuration file for syslogd # # # Full documentation of possible arguments are found in the manpage # syslogd(8). # # # For remote UDP logging use SYSLOGD="-r" # SYSLOGD="-a /var/lib/named/dev/log" |
Restart the logging daemon:
/etc/init.d/sysklogd restart
Start up BIND, and check /var/log/syslog for errors:
/etc/init.d/bind9 start
13 MySQL
In order to install MySQL, we run
apt-get install mysql-server mysql-client libmysqlclient15-dev
You will be asked to provide a password for the MySQL root user – this password is valid for the user root@localhost as well as root@server1.example.com, so we don’t have to specify a MySQL root password manually later on (as was the case with previous Ubuntu versions):
New password for the MySQL “root” user: <– yourrootsqlpassword
We want MySQL to listen on all interfaces, not just localhost, therefore we edit /etc/mysql/my.cnf and comment out the line bind-address = 127.0.0.1:
vi /etc/mysql/my.cnf
[...] # Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. #bind-address = 127.0.0.1 # [...] |
Then we restart MySQL:
/etc/init.d/mysql restart
Now check that networking is enabled. Run
netstat -tap | grep mysql
The output should look like this:
root@server1:~# netstat -tap | grep mysql
tcp 0 0 *:mysql *:* LISTEN 5286/mysqld
root@server1:~#
14 Postfix With SMTP-AUTH And TLS
In order to install Postfix with SMTP-AUTH and TLS do the following steps:
apt-get install postfix libsasl2-2 sasl2-bin libsasl2-modules libdb3-util procmail
You will be asked two questions. Answer as follows:
General type of mail configuration: <– Internet Site
System mail name: <– server1.example.com
Then run
dpkg-reconfigure postfix
Again, you’ll be asked some questions:
General type of mail configuration: <– Internet Site
System mail name: <– server1.example.com
Root and postmaster mail recipient: <– [blank]
Other destinations to accept mail for (blank for none): <– server1.example.com, localhost.example.com, localhost.localdomain, localhost
Force synchronous updates on mail queue? <– No
Local networks: <– 127.0.0.0/8
Use procmail for local delivery? <– Yes
Mailbox size limit: <– 0
Local address extension character: <– +
Internet protocols to use: <– all
Next, do this:
postconf -e ‘smtpd_sasl_local_domain =’
postconf -e ‘smtpd_sasl_auth_enable = yes’
postconf -e ‘smtpd_sasl_security_options = noanonymous’
postconf -e ‘broken_sasl_auth_clients = yes’
postconf -e ‘smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination’
postconf -e ‘inet_interfaces = all’
echo ‘pwcheck_method: saslauthd’ >> /etc/postfix/sasl/smtpd.conf
echo ‘mech_list: plain login’ >> /etc/postfix/sasl/smtpd.conf
Afterwards we create the certificates for TLS:
mkdir /etc/postfix/ssl
cd /etc/postfix/ssl/
openssl genrsa -des3 -rand /etc/hosts -out smtpd.key 1024
chmod 600 smtpd.key
openssl req -new -key smtpd.key -out smtpd.csr
openssl x509 -req -days 3650 -in smtpd.csr -signkey smtpd.key -out smtpd.crt
openssl rsa -in smtpd.key -out smtpd.key.unencrypted
mv -f smtpd.key.unencrypted smtpd.key
openssl req -new -x509 -extensions v3_ca -keyout cakey.pem -out cacert.pem -days 3650
Next we configure Postfix for TLS (make sure that you use the correct hostname for myhostname):
postconf -e ‘myhostname = server1.example.com’
postconf -e ‘smtpd_tls_auth_only = no’
postconf -e ‘smtp_use_tls = yes’
postconf -e ‘smtpd_use_tls = yes’
postconf -e ‘smtp_tls_note_starttls_offer = yes’
postconf -e ‘smtpd_tls_key_file = /etc/postfix/ssl/smtpd.key’
postconf -e ‘smtpd_tls_cert_file = /etc/postfix/ssl/smtpd.crt’
postconf -e ‘smtpd_tls_CAfile = /etc/postfix/ssl/cacert.pem’
postconf -e ‘smtpd_tls_loglevel = 1’
postconf -e ‘smtpd_tls_received_header = yes’
postconf -e ‘smtpd_tls_session_cache_timeout = 3600s’
postconf -e ‘tls_random_source = dev:/dev/urandom’
The file /etc/postfix/main.cf should now look like this:
cat /etc/postfix/main.cf
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
# TLS parameters
smtpd_tls_cert_file = /etc/postfix/ssl/smtpd.crt
smtpd_tls_key_file = /etc/postfix/ssl/smtpd.key
smtpd_use_tls = yes
smtpd_tls_session_cache_database = btree:${queue_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${queue_directory}/smtp_scache
# See /usr/share/doc/postfix/TLS_README.gz in the postfix-doc package for
# information on enabling SSL in the smtp client.
myhostname = server1.example.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = server1.example.com, localhost.example.com, localhost.localdomain, localhost
relayhost =
mynetworks = 127.0.0.0/8
mailbox_command = procmail -a "$EXTENSION"
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
smtpd_sasl_local_domain =
smtpd_sasl_auth_enable = yes
smtpd_sasl_security_options = noanonymous
broken_sasl_auth_clients = yes
smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination
smtpd_tls_auth_only = no
smtp_use_tls = yes
smtp_tls_note_starttls_offer = yes
smtpd_tls_CAfile = /etc/postfix/ssl/cacert.pem
smtpd_tls_loglevel = 1
smtpd_tls_received_header = yes
smtpd_tls_session_cache_timeout = 3600s
tls_random_source = dev:/dev/urandom
|
Restart Postfix:
/etc/init.d/postfix restart
Authentication will be done by saslauthd. We have to change a few things to make it work properly. Because Postfix runs chrooted in /var/spool/postfix we have to do the following:
mkdir -p /var/spool/postfix/var/run/saslauthd
Now we have to edit /etc/default/saslauthd in order to activate saslauthd. Set START to yes and change the line OPTIONS=”-c” to OPTIONS=”-c -m /var/spool/postfix/var/run/saslauthd -r”:
vi /etc/default/saslauthd
# # Settings for saslauthd daemon # # Should saslauthd run automatically on startup? (default: no) START=yes # Which authentication mechanisms should saslauthd use? (default: pam) # # Available options in this Debian package: # getpwent -- use the getpwent() library function # kerberos5 -- use Kerberos 5 # pam -- use PAM # rimap -- use a remote IMAP server # shadow -- use the local shadow password file # sasldb -- use the local sasldb database file # ldap -- use LDAP (configuration is in /etc/saslauthd.conf) # # Only one option may be used at a time. See the saslauthd man page # for more information. # # Example: MECHANISMS="pam" MECHANISMS="pam" # Additional options for this mechanism. (default: none) # See the saslauthd man page for information about mech-specific options. MECH_OPTIONS="" # How many saslauthd processes should we run? (default: 5) # A value of 0 will fork a new process for each connection. THREADS=5 # Other options (default: -c) # See the saslauthd man page for information about these options. # # Example for postfix users: "-c -m /var/spool/postfix/var/run/saslauthd" # Note: See /usr/share/doc/sasl2-bin/README.Debian OPTIONS="-c -m /var/spool/postfix/var/run/saslauthd -r" |
Now start saslauthd:
/etc/init.d/saslauthd start
To see if SMTP-AUTH and TLS work properly now run the following command:
telnet localhost 25
After you have established the connection to your Postfix mail server type
ehlo localhost
If you see the lines
250-STARTTLS
and
250-AUTH PLAIN LOGIN
everything is fine.
The output on my system looks like this:
root@server1:/etc/postfix/ssl# telnet localhost 25
Trying 127.0.0.1…
Connected to localhost.localdomain.
Escape character is ‘^]’.
220 server1.example.com ESMTP Postfix (Ubuntu)
ehlo localhost
250-server1.example.com
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-AUTH PLAIN LOGIN
250-AUTH=PLAIN LOGIN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
quit
221 2.0.0 Bye
Connection closed by foreign host.
root@server1:/etc/postfix/ssl#
Type
quit
to return to the system’s shell.
15 Courier-IMAP/Courier-POP3
Run this to install Courier-IMAP/Courier-IMAP-SSL (for IMAPs on port 993) and Courier-POP3/Courier-POP3-SSL (for POP3s on port 995):
apt-get install courier-authdaemon courier-base courier-imap courier-imap-ssl courier-pop courier-pop-ssl courier-ssl gamin libgamin0 libglib2.0-0
You will be asked two questions:
Create directories for web-based administration ? <– No
SSL certificate required <– Ok
If you do not want to use ISPConfig, configure Postfix to deliver emails to a user’s Maildir*:
postconf -e ‘home_mailbox = Maildir/’
postconf -e ‘mailbox_command =’
/etc/init.d/postfix restart
*Please note: You do not have to do this if you intend to use ISPConfig on your system as ISPConfig does the necessary configuration using procmail recipes. But please go sure to enable Maildir under Management -> Server -> Settings -> EMail in the ISPConfig web interface.
16 Apache/PHP5
Now we install Apache:
apt-get install apache2 apache2-doc apache2-mpm-prefork apache2-utils libexpat1 ssl-cert
Next we install PHP5:
apt-get install libapache2-mod-php5 php5 php5-common php5-curl php5-dev php5-gd php5-idn php-pear php5-imagick php5-imap php5-json php5-mcrypt php5-memcache php5-mhash php5-ming php5-mysql php5-ps php5-pspell php5-recode php5-snmp php5-sqlite php5-tidy php5-xmlrpc php5-xsl
You will be asked the following question:
Continue installing libc-client without Maildir support? <– Yes
Next we edit /etc/apache2/mods-available/dir.conf:
vi /etc/apache2/mods-available/dir.conf
and change the DirectoryIndex line:
<IfModule mod_dir.c>
#DirectoryIndex index.html index.cgi index.pl index.php index.xhtml
DirectoryIndex index.html index.htm index.shtml index.cgi index.php index.php3 index.pl index.xhtml
</IfModule>
|
Now we have to enable some Apache modules (SSL, rewrite, suexec, and include):
a2enmod ssl
a2enmod rewrite
a2enmod suexec
a2enmod include
Reload the Apache configuration:
/etc/init.d/apache2 force-reload
16.1 Disable PHP Globally
(If you do not plan to install ISPConfig on this server, please skip this section!)
In ISPConfig you will configure PHP on a per-website basis, i.e. you can specify which website can run PHP scripts and which one cannot. This can only work if PHP is disabled globally because otherwise all websites would be able to run PHP scripts, no matter what you specify in ISPConfig.
To disable PHP globally, we edit /etc/mime.types and comment out the application/x-httpd-php lines:
vi /etc/mime.types
[...] #application/x-httpd-php phtml pht php #application/x-httpd-php-source phps #application/x-httpd-php3 php3 #application/x-httpd-php3-preprocessed php3p #application/x-httpd-php4 php4 [...] |
Edit /etc/apache2/mods-enabled/php5.conf and comment out the following lines:
vi /etc/apache2/mods-enabled/php5.conf
<IfModule mod_php5.c> #AddType application/x-httpd-php .php .phtml .php3 #AddType application/x-httpd-php-source .phps </IfModule> |
Then restart Apache:
/etc/init.d/apache2 restart
17 Proftpd
In order to install Proftpd, run
apt-get install proftpd ucf
You will be asked a question:
Run proftpd from inetd or standalone? <– standalone
Then open /etc/proftpd/proftpd.conf and change UseIPv6 from on to off; otherwise you’ll get a warning like this when you start Proftpd:
If you get a message like this:
– IPv6 getaddrinfo ‘server1.example.com’ error: Name or service not known
you can either modify /etc/hosts and add server1.example.com to the ::1 line:
vi /etc/hosts
127.0.0.1 localhost.localdomain localhost 192.168.0.100 server1.example.com server1 # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback server1.example.com fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters ff02::3 ip6-allhosts |
… or you can open /etc/proftpd/proftpd.conf and change UseIPv6 from on to off
vi /etc/proftpd/proftpd.conf
[...] UseIPv6 off [...] |
For security reasons you can also add the following lines to /etc/proftpd/proftpd.conf (thanks to Reinaldo Carvalho; more information can be found here: http://proftpd.org/localsite/Userguide/linked/userguide.html):
vi /etc/proftpd/proftpd.conf
[...] DefaultRoot ~ IdentLookups off ServerIdent on "FTP Server ready." [...] |
ISPConfig expects the configuration to be in /etc/proftpd.conf instead of /etc/proftpd/proftpd.conf, therefore we create a symlink (you can skip this command if you don’t want to install ISPConfig):
ln -s /etc/proftpd/proftpd.conf /etc/proftpd.conf
Then restart Proftpd:
/etc/init.d/proftpd restart
18 Webalizer
To install webalizer, just run
apt-get install webalizer
19 Synchronize the System Clock
It is a good idea to synchronize the system clock with an NTP (network time protocol) server over the internet. Simply run
apt-get install ntp ntpdate
and your system time will always be in sync.
20 Install Some Perl Modules Needed By SpamAssassin (Comes With ISPConfig)
Run
apt-get install libhtml-parser-perl libdb-file-lock-perl libnet-dns-perl
21 ISPConfig
The configuration of the server is now finished, and if you wish you can now install ISPConfig on it. Please check out the ISPConfig installation manual: http://www.ispconfig.org/manual_installation.htm
21.1 A Note On SuExec
If you want to run CGI scripts under suExec, you should specify /var/www as the home directory for websites created by ISPConfig as Ubuntu’s suExec is compiled with /var/www as Doc_Root. Run
/usr/lib/apache2/suexec -V
and the output should look like this:
root@server1:~# /usr/lib/apache2/suexec -V
-D AP_DOC_ROOT=”/var/www”
-D AP_GID_MIN=100
-D AP_HTTPD_USER=”www-data”
-D AP_LOG_EXEC=”/var/log/apache2/suexec.log”
-D AP_SAFE_PATH=”/usr/local/bin:/usr/bin:/bin”
-D AP_UID_MIN=100
-D AP_USERDIR_SUFFIX=”public_html”
root@server1:~#
So if you want to use suExec with ISPconfig, don’t change the default web root (which is /var/www) if you use expert mode during the ISPConfig installation (in standard mode you can’t change the web root anyway so you’ll be able to use suExec in any case).
The following screenshot is taken from an ISPConfig installation in expert mode. If you want to use ISPConfig, then don’t change the default web root:
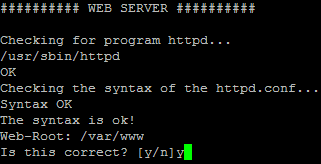
22 Links
- Ubuntu: http://www.ubuntu.com
- ISPConfig: http://www.ispconfig.org






I think the admin of this web site is in fact working hard in favor of his web site, since here every stuff is quality based information.